If you forget the key of ESET Windows standard encryption function "bitlocker"!?
This article is re -edited the "how to deal with the" BitLocker recovery key "published in the" Cyber Security Information Bureau "provided by Canon Marketing Japan.
With the spread of remote work, Bitlocker is standard on Windows, which helps reduce the risk of leakage in the case of loss and theft.In this use, it is important to manage the recovery key issued by encryption.In this article, we will explain how to deal with the recovery key while looking back on the importance of storage encryption.
The importance of encryption by bitlocker
Bitlocker is a function to encrypt the storage, which is standard on the Windows OS.The advantage is that even if you lose or steal a computer used in your work, you can reduce the risk of saved data by reading the saved data.
In recent years, the need for storage encryption has increased.The main reason is that the number of people who work out of the company to take out laptops out of the company and do business is increasing due to the corona evil.As a result, it is necessary to deal with laptops loss and theft risk.
Many of them have a search function for devices that identify the current location as a measure to lose and theft of personal computers.There is also a method of protecting OS and BIOS with a password and increasing security strength.However, even if you set up a login password, it is possible to extract data from the laptop computer physically, and it is not always safe.
Assuming such a risk, Bitlocker, which encrypts storage, can be an effective security measure for Windows users.
How to set BitLocker
In an environment where laptops are distributed by companies and organizations, BitLocker is often set by system administrators at once.In the case of a laptop that is distributed and rented, some of the encryption settings may have already been supported.
On the other hand, if the user himself sets Bitlocker, it is assumed that the Windows 10 Pro version is used.In addition, it is necessary to log in with an administrator privilege that can be set.
Bitlocker setting will take the following steps.
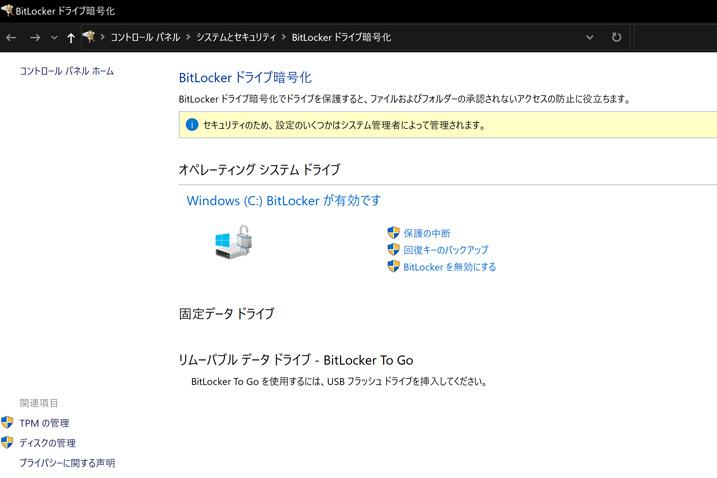
・ “Control Panel”> “System and Security”> Select Bitlocker Drive Cryptography ・ Enable BitLocker ⦁ Specify how to backup of recovery key.
Bitlocker drive encryption screen
Then, specify the backup method of the recovery key, select the range of encryption and encryption mode.When these steps can be ready for encryption, the computer is restarted through the system check.After that, the encryption process progresses in the background, and the BitLocker setting is completed.
The above recovery key is composed of a 48 -digit string, and is used to unlock BitLocker.Specifically, the login may be required to enter a recovery key if the login fails a certain number of times or a problem with hardware.If you lose the recovery key, you will not be able to access the storage, so you must back up.
At the time of shipping, BitLocker has already been enabled at the time of shipment.In that case, the above settings are not required, but we want to make a backup of the recovery key as soon as possible.
How to deal with the recovery key
When the initial setting of a laptop computer is performed, many users may check and change the settings of BitLocker.Many users should be unknown the recovery key after the time has passed since the initial settings.The backup of the recovery key is often performed in the following method, so if you lose it, you should try it step by step.
1) Check your Microsoft account
Bitlocker recovery key can be easily stored in a Microsoft account when setting.Therefore, it seems that many users have forget the saved itself.First, log in to your Microsoft account to see if the recovery key is stored.At the time of logging in, the registered ID and password are required, so I want to keep them properly.
In some cases, a laptop computer cannot be used because the recovery key is not found.In that case, you can log in to a Microsoft account from another computer and find a recovery key stored online.
2) Find the printed paper
When setting BitLocker, you can choose to print the recovery key on paper.Users and organizations that have the habit of printing important information on paper may choose printing.It is a good idea to check if the recovery key is printed on the document that was organized when purchasing a laptop.
3) Find a saved text file
Bitlocker recovery key has the option to save it as a text file.In that case, it is possible to connect to another computer and check the recovery key.In the initial setting, the text file contains a "bitlocker" string, so it is possible to search for USB drive etc. each.
In some cases, companies and organizations are managing computers, and in some cases, in -house devices are managed using Active Directory.In this case, the administrator knows the recovery key, so you may want to contact the administrator.
Bitlocker is considered to be stored in any location to demand the recovery key backup in the setting process.Considering the loss risk of the recovery key itself, many users may be saved in the Microsoft account that makes it easier to manage online.
Users with computer administrator privileges can disable Bitlocker.However, considering the risk of information leakage, disabling is not recommended.
Advanced encryption solutions in terminals
BitLocker is easy to introduce and can be managed via Active Directory, but more robust measures may be required when using it in companies and organizations.Specifically, it is considered to be more desirable to introduce a solution that can encrypt the entire hard disk than Bitlocker, which is encrypted on a drive -by -one.For example, ESET ENDPOINT ENCRYPTION, an endpoint countermeasure product that has a function based on the encryption of a hard disk, strongly protects the terminal with advanced functions.
1) Encrypted with full disk instead of drive units
Encrypt the hard disk or SSD built into the computer on the entire disk or partition.The encryption algorithm uses AES256bit, which is said to be the most robust method.It is almost impossible to read the data even if the storage is extracted by encryption.
2) Management functions such as checking encryption status, policies in bulk distribution, etc.
A computer with a program for endpoints and its owners can be displayed and managed in a list.Confirm the status of full -isk encryption and maintain a safe condition.It is also possible to apply different policies for each group by performing computer settings via the network.
3) Sufficient support
Bitlocker is a standard function, so its support is limited to forums.In the case of corporate support provided by EndPoint Encryption, the burden on information security representatives will be reduced because individual problems occur.
It is expected that remote work will continue to spread and continue, and the use of digital devices is expected to accelerate, and it is certain that the importance of terminal management, including laptops, will increase.Companies and organizations that handle important information, including personal information, should also consider the introduction of IT solutions, which realizes advanced encryption, as part of higher levels of risk management.






![[July 6 and 7] DX realized by content cloud, advanced platform for business transformation](https://website-google-hk.oss-cn-hongkong.aliyuncs.com/drawing/article_results_9/2022/3/9/6bbafe438d78271513761788166cbf94_0.jpeg)

