What will change with the new Wi-Fi security standard "WPA3"? Industry group explains
On June 28, 2018, the Wi-Fi Alliance, an industry group that conducts interoperability testing and certification of wireless LAN products, announced the new security specification "Wi-Fi CERTIFIED WPA3" and IoT device connectivity. A press briefing will be held to introduce new specifications such as "Wi-Fi CERTIFIED Easy Connect" that simplifies settings and "Wi-Fi CERTIFIED Enhanced Open" that encrypts communications even in open Wi-Fi environments without connection authentication. held.
Kevin Robinson, VP of Marketing, Wi-Fi Alliance, at the briefing
WPA3: password authentication is more robust, enterprises add 192-bit encryption
WPA3 is the next-generation Wi-Fi to replace WPA2, which was formulated in 2004 and has been in use for over 10 years. -Fi security specification. It stipulates methods of "authentication" when a wireless LAN access point (AP) permits device connection, and "encryption" to protect communication traffic exchanged between the two after connection. Currently, in order for wireless LAN devices to receive Wi-Fi CERTIFIED certification, it is necessary to implement WPA2, but in the future WPA3 will become a mandatory requirement instead.
Similar to WPA2, WPA3 also offers two operation modes: "WPA3 Personal" for homes/small offices and "WPA3 Enterprise" for large offices. And in any of them, new security technology is added to realize a more robust Wi-Fi environment. The "KRACK" vulnerability discovered in WPA2 last year has also been resolved in WPA3.
Two operation modes are available: "WPA3 Personal" for homes/small offices and "WPA3 Enterprise" for large offices.
WPA3 Personal requires a single password to be entered when authenticating the connection to the AP. This authentication method is the same as WPA2-Personal (WPA2-PSK: pre-shared key method), but WPA3 ``even though it is password-based, provides more robust security (than WPA2-PSK),'' he said. Fi Alliance VP of Marketing Kevin Robinson explained.
Specifically, SAE (Simultaneous Authentication of Equals) has been added as a key establishment protocol for authentication. SAE does not exchange the password itself between the AP and the device, but rather exchanges multiple times "problems/answers for which the correct answer can be obtained by calculating using the correct password", which is an effective attack method for WPA2-PSK. makes offline dictionary/brute force attacks virtually impossible. It is also more resistant to attacks than WPA2-PSK, even if you use passwords that do not meet the recommended length/complexity.
In addition, even if the password is leaked/decrypted by an attacker, "Forward Secrecy (future confidentiality)" is realized so that the content of the encrypted traffic captured (eavesdropped) in the past will not be decrypted. Mr Robinson explained. This also disables the attack method that was an issue with WPA2. Specifically, by generating a new (unique) session key in the SAE handshake, even if the password is leaked, the past session key cannot be obtained and the contents of communication cannot be deciphered. there is
``Of course, using a password that is not long enough or complicated can be a vulnerability (increases the possibility that an attacker can infiltrate the network), but the forward secrecy of the communication content is guaranteed. is stolen, the (previously captured) traffic remains confidential," Robinson said.
On the other hand, WPA3 Enterprise, which uses the IEEE 802.1x authentication server, also adds a new 192-bit CNSA (Commercial National Security Algorithm) as a communication encryption algorithm option. CNSA, which is also used by the US NSA (National Security Agency) for government communication, is an algorithm that realizes communication encryption with even higher strength than AES (Advanced Encryption Standard) used in WPA2. Robinson said it would be particularly useful for wireless networks in organizations requiring the highest level of communication security, such as government agencies, finance and healthcare.
By the way, if you select this CNSA 192-bit encryption mode, we also provide a mechanism to prevent network administrators from accidentally setting other (lower strength) modes when configuring individual APs. It is said that This prevents the occurrence of "weakest links" within the organizational network and maintains the robustness of the entire network.
Outline of "Wi-Fi CERTIFIED WPA3"
Mr. Robinson commented on the spread of wireless LAN products (APs, controllers, devices) that implement WPA3 in the market. It may be in a situation where it is compatible with WPA3," he said. Most of the technologies, except for CNSA 192-bit encryption, can be implemented on a software basis, so it is possible that some existing products will support WPA3.
At the moment, the Wi-Fi Alliance continues to require the implementation of WPA2 for Wi-Fi CERTIFIED certification. is a mandatory requirement.
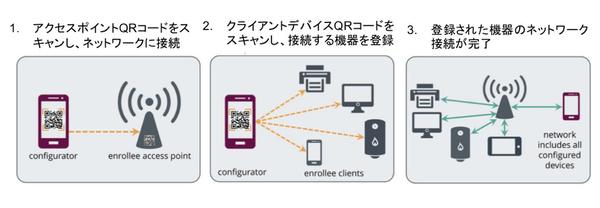
Easy Connect: Easy connection by reading the device's QR code with a smartphone
Wi-Fi CERTIFIED Easy Connect is a certification standard for a new connection setting method for smart home devices and IoT devices. Since it supports WPA2/WPA3, there is a possibility that devices that adopt this method will appear even before the spread of WPA3.
Mr. Robinson said that many of these new types of devices do not have keyboards, buttons, displays, etc., so Easy Connect was formulated to simplify Wi-Fi connection settings. talk. The Wi-Fi Alliance has already developed the WPS (Wi-Fi Protected Setup) specification, which simplifies connection setup, but WPS requires pressing a button on the device or entering a PIN code. rice field.
The specific way to use Easy Coonect is to use the app installed on your smartphone or tablet and the built-in camera to simply scan the 2D barcode attached to the device (or attached in the form of a card, etc.). As a result, security settings such as connection settings to the device's Wi-Fi AP and WPA2/WPA3 passwords are automatically performed.
How to use "Wi-Fi CERTIFIED Easy Connect"
Enhanced Open: Connect without a password, traffic is encrypted
Wi-Fi CERTIFIED Enhanced Open is a security issue in open Wi-Fi that allows use without authentication such as public wireless LAN It is a new specification that solves
Public wireless LANs provided at airports, train stations, stadiums, public buildings, etc. do not apply security standards such as WPA2 in order to realize the convenience of allowing users to connect to APs without entering a password. It is often "open Wi-Fi". However, open Wi-Fi does not encrypt the communication traffic between the device and the AP, and there is a risk of eavesdropping by an attacker. Therefore, until now, users had to protect themselves by using a separate VPN.
Enhanced Open, announced in early June, is a standard that realizes a secure Wi-Fi environment that encrypts communication while maintaining the convenience of not having to enter a password. Specifically, it uses a key-establishment protocol called Opportunistic Wireless Encryption (OWE) to generate a cryptographic key for each client, and then combines it with other cryptographic protocols to encrypt traffic. According to the Wi-Fi Alliance's announcement, open Wi-Fi that already has a captive portal (web portal displayed when connecting) does not require an additional authentication server, so current It is possible to maintain a simple environment as it is.
Outline of "Wi-Fi CERTIFIED Enhanced Open"
In addition, the product certification programs for each of the WPA3, Easy Connect, and Enhanced Open standards introduced this time have already started.






![[July 6 and 7] DX realized by content cloud, advanced platform for business transformation](https://website-google-hk.oss-cn-hongkong.aliyuncs.com/drawing/article_results_9/2022/3/9/6bbafe438d78271513761788166cbf94_0.jpeg)

