ASCII.jp Someone is looking from a network camera
Those who hide at the end of the network camera
In 2013, a network camera set up in the Srek family living in Ohio, USA suddenly shouted, "Wake up! Wake up!"The network camera was installed to watch her 10 months old daughter Emma, but when her father, Adam, jumped up and entered her daughter's bedroom, the camera is now obscene words.I started calling.The scary Adam immediately pulled out the camera plug and turned off the power.However, at the same time, the logs of the IP address set up in the camera and the traces of the hackers hijacked this camera have disappeared.
An article on the newspaper company San Francisco Chronicle's website SFGate.
The network camera used in the Schrek family was the latest IP camera from FOSCAM in China.The incident occurred in the spring of 2013, and FOSCAM introduced an emergency software patch in July 2013, but scanned as a result of a survey by Qualys, a vulnerability diagnosis and management service.Of the 46,000 FOSCAM, 40,000 units did not apply this patch..COM tells you.
An article by Forbes telling a post -survey.
In fact, the hacking damage of these network cameras occurs relatively frequently.increase.Especially in China, the number of people who install network cameras at home is increasing, and there are no spare time in such damage.
In China, which is rampant, there are 2,000 groups of 2,000 groups that exchange IP addresses of network cameras that can be peeked on the popular chat software "QQ" in the country, and in Zhejiang Province, in Zhejiang Province.A man who sold a tool to hack a network camera account was arrested.This man uses this tool himself and hacks 10,000 network cameras.A part of the video was published on SNS, and the recommended peeping camera IP address was sold for 20 yuan (about 340 yen).
An article in the southern city newsletter reporting the case in Zhejiang Province.The existence of the outright group by QQ and some of the video of the IP camera sold are also introduced in photos.
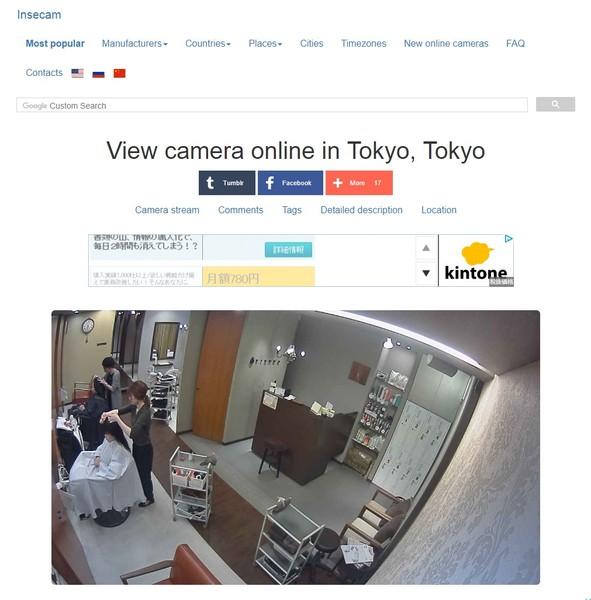
In addition, Russia has a site called Insecam that covers video of IP cameras, such as security cameras, security cameras, and fixed -point observation cameras installed around the world.This site also has many Japanese live cameras IPs, and anyone can view them freely.Some cameras are photographed inside the store, the storefront, and the front of the house, so the video of the camera that would probably be installed for security can be seen by anyone, which is rather dangerous.It is in a state.
A video of a web camera installed at a Tokyo hair salon that can still be seen on Inscam.It is clearly visible to customers.
In the IT scene, IoT devices that connect everything to the Internet are trends, but malicious hackers are also targeted for these IoT devices.
The day when TV demands ransom
And the most advanced net threat trend is ransomware.This malware, which demands ransom to get a passcode for screens and unlocks infected electronic devices, has recently been rampant, not only for PCs but also on smartphones.
The attention here is a smart TV that has begun to spread these days.
On December 25, 2015, Darren Carson, a software developer in Kansas, USA, reported on Twitter that "a family was infected with a ransomware when a family downloaded a movie viewing app on a smart TV."It was an Android -based smart TV of LG Electronics.
The ransom request is $ 500.It was said that it would cost $ 340 to contact LG Electronics and get a technician to get support.Either way, the appropriate investment was forced.
Darren Carson's tweet.An acquaintance's smart TV reported that the screen was locked on a screen imitating the FBI warning.
Eventually, it seems that the restoration mode was launched by pressing two physical buttons on the TV in a specific order in a proposal of LG Electronics, and returning to the state at the time of shipment, it seems that there was nothing.The introduction of security software like a PC will increase the number of threats targeting smart home appliances that cannot take self -defense means.
Household appliances that involve the war without knowing
Well, finally, a bigger and scary story.
In November 2016, about 1 million European users became unable to access the Internet.The router used by German Telecom users, a major German provider, is the target of the malware "MIRAI", but the router with about 900,000 units has been botted net, and it is for the attack that was made to be the leader of the DDOS attack.rice field.
An article on the news site of Romanian security software vendor "BitDefender".
DDOS is a cyber attack method that sends a large amount of traffic to the target server and computer to stop functioning.In recent years, the target of botization is not a PC, but an IoT device such as routers and smart home appliances.And the background is the existence of the malware "MIRAI".
"MIRAI" is randomly searched for an IoT device IP address and finds an accessible IoT device in malware searching for infection, and for example, "Adimin", for example, "Adimin".Try logging in with a combination that is common in initial settings, such as "user", "Password" and "0000".If you succeed in logging in, search for the IoT device around it and try to log in as well.In this way, the number of infected terminals is increased one after another, and a large -scale botted IoT device is created.IoT devices infected with MIRAI are sometimes slowed down, but they are not easily infected because they do not hinder their original functions.
そうしてハッカーが操作するC&C(コマンド&コントロール)サーバーからの指示を待ち、ひとたび指示が下れば、特定のIPアドレスに対し、一斉にパケットを送り続け、標的となったサーバーのリソースを枯渇させて、機能不全の状態に陥れるのです。
It is said that this case, aiming for a German telecom router, was due to an attack that was newly tried to incorporate a router under the German Telecom into a MIRAI botnet network, but why such a large -scale botnet.Is it necessary to create?
In fact, it is rumored that these botnet networks are traded in the black market on the back.Hackers with a botnet sell their own botnet network at time, which makes hackers get money, and attackers can perform cyber attacks without their technical skills.is.
Currently, MIRAI is said to have a weak security IoT device incorporated into a botnet, but according to Bit Defender, a Romanian security software vendor, about the approximate smart device currently connected to the Internet.2 % reported that the Telnet service password is weak or not at all.2 % may not feel so large, but about 128 million smart devices have potentially botting vulnerabilities.
However, even if your IoT device attacks a server you don't know anywhere, you may think that there is no significant damage to you.But things are not so simple.
For example, what if the target server is a server involved in defense?Or what if it was a financial institution's server?What if it was a medical institution's server?
North Korea is still nervous, but North Korea is said to use a similar botnet to make cyber attacks on the United States.The FBI and the US Ministry of Land Security announced that the hacker group in charge of North Korea's cyber attacks is called Hidden Cobra (hidden Cobra), and that it is using a DDOS tool called "DELTACHARLIE" to attack DDOS.I am."DeltaCharlie" is said to be the third botnet of HiddenCobbra following "Deltaalpha" and "DeltaBravo", and is a botanet targeting the ended Windows PC, but in the near future, in the near future.With the botnet of 4, the home appliances of your house may be involved in the North Korean cyber attack without knowing it.




![[July 6 and 7] DX realized by content cloud, advanced platform for business transformation](https://website-google-hk.oss-cn-hongkong.aliyuncs.com/drawing/article_results_9/2022/3/9/6bbafe438d78271513761788166cbf94_0.jpeg)

