ASCII.jp Telework VPN required is performance, expandability, and vulnerability measures
Many companies heard that "VPN capacity is not enough" in the Corona evil this time.For a company where cloudization is in the middle of the road, VPN is essential to access internal systems.Here, I would like to consider the existing VPN environment issues and updates.
VPN environment of companies that did not assume telework
VPN is a technology that builds a highly secure communication route on a shared network that allows you to play highly confidential corporate applications with confidence.It is called Virtual Private Network = VPN to achieve the same communication environment as "dedicated lines" that directly connect corporate networks by physical line with a public network like the Internet.
The actual situation of VPN is a collection of network security technologies such as data encryption, falsification detection, and telecommunications partner authentication, and many are standardized as the standard technology for the Internet.If network devices such as routers and firewalls support these VPN functions, you can build secure communication routes (tunnels) by VPN.In the 1980s and 1990s, most of these security technologies were vendor -specific, so the standardization of the standards was generalized.Now, low -priced routers have a VPN function, and even without expensive dedicated lines, you can easily build high security networks.
VPN that connects companies, branch offices, sales offices, homes, etc. with a closed network
In companies, VPNs are used in remote access to the bases in addition to the site (VPN between sites) (remote access VPN).If a corporate IT system is installed in an in -house server room or data center, the latter remote access VPN is required when employees use them from home or on the go.
Nevertheless, for the VPN between sites that build VPN between VPN routers, remote access VPN must introduce dedicated VPN software for each PC used by employees, so it is troublesome to introduce it.It will take.Moreover, the router firewall on the remote access side requires specifications that can withstand simultaneous access, and it is difficult to expand in the case of hardware.In the first place, the corporate system so far does not assume the state of "telework", and there is no VPN environment for employees.With these issues, it was difficult to improve the environmental development of remote access VPN, which is the premise of telework.
VPN issues in telework
Under these circumstances, many companies faced the challenge of "lack of VPN capacity" in the development of teleworking environments in Corona.If there is not enough VPN, employees will not be able to access the files and systems required for their work, making it difficult to work from home.Companies that cannot expand VPNs have restricted the time zone at which VPNs can be used, and the use of VPNs in each department's circular number has survived the employment at the time of emergency declaration, but many dissatisfactions have occurred from the site.It's not hard to imagine.
In addition to the expansion of hardware, the introduction of cloud -based services
So, how should companies that consider working from home consider infrastructure in the future?Many companies are promoting the cloud migration of IT systems in the company and data centers in the company or data center, but companies that are still unable to move will need to improve VPN performance and capacity.
The simplest way is to add VPN routers and firewalls.The latest hardware equipped with a dedicated chip has a perfect number of VPN tunnels and performance, and it is possible to set detailed settings such as security, routing, and QOS, so if you can get the resources for operation management in the information system department, it is a recommended choice.。Recently, the number of managed security services that can outsource the settings and operations to businesses at monthly fees is increasing, so if the information system department is lacking in specialty and resources, it is good to consider such services.
Difference between hardware VPN and cloud type VPN
On the other hand, if you value the introduction speed, we recommend a cloud -type VPN service that does not require hardware.It can be used by introducing a VPN client on the end user's device, and can be accessed to the company's internet and mobile environments to the company's internal system.The latest services not only on -premises, but also covers closed connections to cloud services, so they can be connected seamlessly without being aware of both, two -step authentication and fine access control to prevent spoofing and unauthorized access., Access log management function is provided.Above all, it is possible to scale out and scale in without the addition of devices, so that the cost can be optimized according to the usage trends.
Building and expansion of VPN environments, most of all, vulnerability measures
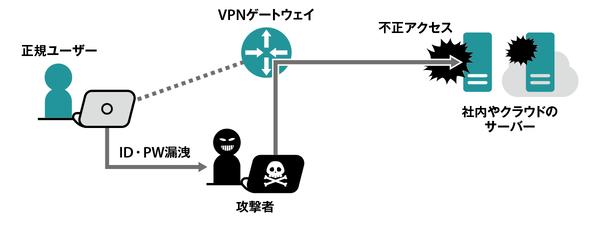
Another thing to consider in VPN is security.With the spread of telework, the VPN has become familiar at once, but the number of attacks aimed at VPN to keep pace with this is increasing.Specifically, by hitting the vulnerability of the VPN gateway that accepts remote access, the ID and password are fraudulent and invades the internal network via the VPN instead of the user.
Unauthorized access to vulnerability of VPN gateway
The other day, it was reported that VPN users' IDs and passwords may have leaked in Pulse Cure's SSL VPN devices.JPCERT/CC and each media, which provide security information, have warned for a long time regarding vulnerabilities, and the company's SSL VPN devices have distributed patches to eliminate vulnerabilities and have encouraged users.。Nevertheless, it seems that the attacked company's devices were not patched, and the IP address list of the non -patched devices was released on the dark web, so it seems to have been attacked.
Due to this background, in a sense, it is a user company's "self -employed self -benefit", but the construction of an emergency telework system may have leaked measures.Nevertheless, it is only dangerous to have a hole in a security device for using a corporate network with confidence, so the applying patch should be the top priority.In addition, companies that are not confident in operation would like to consider the introduction of a managed service, including the application of the patch.




![[July 6 and 7] DX realized by content cloud, advanced platform for business transformation](https://website-google-hk.oss-cn-hongkong.aliyuncs.com/drawing/article_results_9/2022/3/9/6bbafe438d78271513761788166cbf94_0.jpeg)

