ASCII.jp The latest tricks of net threats you don't know
The temperature is getting warmer, and there are many people who have a new gate.In order to make your new life enjoyable and secure, you should also pay attention to the security around the digital.
Although the media has become noisy for a while, the threat of the web, such as viruses, personal information acquisition, and monetary demands, is still appearing one after another.In addition, not only devices such as personal computers and smartphones, but in recent years, smart home appliances and IoT equipment have become connected to the Internet, and attacks that have pierced those vulnerabilities have increased.Here are some of the threats of the Internet that will not be able to do it because you are relieved because you have a security software.
The actual situation of the threat of the web targeting IoT equipment
If you are conscious of security, you will have security software on your computer.In addition, some people may have installed security software on smartphones and have a perfect system.Indeed, if security software is introduced, those devices will be protected by external attacks.However, how many people are paying attention to devices that cannot install software, such as smart TVs, smart speakers, game equipment, network cameras, and various IoT equipment that control home appliances?
In recent years, malware targeting such defenseless IoT equipment has been increasing.Here are new internet threats targeting recently newly confirmed IoT devices.
"Reaper" to increase the first soldier of DDOS attacks
In October 2017, the existence of malware called "Reaper" aimed at IoT equipment was confirmed."Reaper" is a malware that hijacks the device by hitting a known vulnerabilities and botting it to remotely control it.The target is a variety of network cameras, NAS, servers, routers, etc. equipped with Linux -based OSs, and it is said that millions have already been said to be millions that have been infected with this malware.It is said that a botnet is built.
Once an attacker is issued by an attacker, the infected device will launch DDOS and other attacks all at once.
The scary thing about the bot is that unless a remote control order is given, it is unknown that it is lurking quietly and infected with the user.And if an attack order is issued, you will become a perpetrator who will cause a large -scale disability without knowing it.This Reaper can send and attack program sources, which can cause more damage than DDOS.
Reference: Bot "Reaper" aiming for IoT devices, infection with millions of network devices
"Brickerbot" that makes IoT equipment unusable
"Brickerbot", which was confirmed in April 2017, is a malware that makes IoT equipment completely unusable, and is worse than bots.The attack method is to connect a total hit attack aiming for the initial setting ID and password of the IoT device.By changing the set value, hindering the connection to the Internet, reducing the operation, or deleting the files in the device, executing an unauthorized Linux command will eventually fall into use.。
Be careful not to use IoT devices that have been introduced to live a more comfortable life because of the lack of security management.
Reference: Malware that makes IoT devices "unusable", "Brickerbot"
"PERSIRAI" to bot a network camera
"PERSIRAI" is a malware that invades the management screen of the network camera, abuses the open port, runs a command, and dung and botes malware.While following the conventional malware infection method, new methods are incorporated, and the influential network camera is over 1000 models.It has the ability to infect not only DDOS attacks with remote orders, but also other network cameras one after another.
Reference: "PERSIRAI" that botes a network camera
Although the number of IoT equipment, including smart speakers, is increasing, unlike information terminals such as PCs and smartphones, there are many percentage of people who introduce them in a sense of home appliances, and the security awareness of users is still so high.do not have.The login ID and password remain in the initial state, or the update is neglected and there are no vulnerability measures.However, as long as the network is connected, it is necessary to change the awareness that any device will be amazing.
All network connected devices need security measures!
In this way, in modern times, not only PCs and smartphones, but also all network connection devices in the home are threatened.Security measures are indispensable to protect such threats.
Many people think "I'm okay."But it's too late after being damaged.First of all, be sure to introduce security software on your computer or smartphone.
PCs and smartphones can be taken with security software, but what should I do with IoT equipment?Therefore, I would like to recommend the trend micro "Virus Buster for Home Network", which can protect network connection devices at home.
↑ Package of the trend micro "virus buster for home network".It is necessary to update the service contract every year
"Virus Buster for Home Network" is a hardware -type security device in a palm -sized black box.Just connecting to a router and installing the app on the smartphone or tablet of the management?
↑ The palm -sized body is very simple
To easily introduce the mechanism, all network connection devices are always exchanged through routers when communicating with the outside.By incorporating this product into a home network, checking the communication of PCs, smartphones, and IoT equipment through the router, blocking access to malicious sites, blocking unauthorized communication, invading malware?It is possible to prevent it before.
↑ Just connect the power and connect the wired LAN port to the router.Wait for a few minutes until the LED lamp turns green
The settings are set from the smartphone or tablet management app.In the management app, all devices connected to the network can be visualized and you can register the users on each device.By doing so, you can check that the non -actually used devices are connected to the home network, and to restrict access to adult sites and dating sites on your child's smartphone, or overdo the game.In order to deal with, it is possible to decide the time when the Internet can be used.
* Effective functions for devices connected to a network at home.
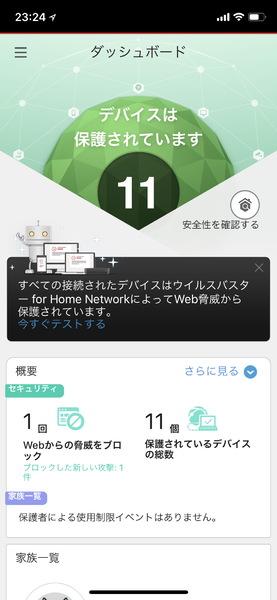
↑ Security information can be checked together, and filtering can be set for all devices.If you register the user in the device, it is possible to set it for each user.
Even without special settings, you can block access to fraudulent sites and monitor the network into the network, and protect them from unauthorized remote control.Security devices are painful to realize the benefits, but since communication history is left, what kind of attack you were attacked, what sites you tried to access, and are frequently used apps on smartphones.You can check the usage status.You can always see how the IoT devices used at home are protected, so they dispel the anxiety, "Is this box working properly?"
↑ If you turn on the notification, you will be notified to the management app and the history will remain.
Spring, where the year changes and new life, such as new members of society, enrollment and advancement, is a good opportunity to review home security.Now that IoT devices are growing in the home, we will introduce the "Virus Buster for Home Network" immediately to protect the safety of the home.
* This product is effective when you want to protect Internet connection devices that cannot install security software from hijacking or remote control, or want to defend access to harmful sites at once.
* Since USB memory and virus attached to e -mails are not attacked on the network, or when using terminals outside the network at home, it is not eligible for protection of this product, so PCs and smartphones are conventional security.I need software.
Provided: Trend Micro




![[July 6 and 7] DX realized by content cloud, advanced platform for business transformation](https://website-google-hk.oss-cn-hongkong.aliyuncs.com/drawing/article_results_9/2022/3/9/6bbafe438d78271513761788166cbf94_0.jpeg)

